F5 secures applications and therefore, the data and intellectual property behind them— that is where today’s attacks happen.
With a background devoted to connecting users and applications, their solutions provide unparalleled visibility into hidden threats and offer the controls needed to manage access and reduce the risks of application attacks. Their solutions support security for any infrastructure, from traditional data centres to cloud environments. This means our clients can securely access data on any device, in any environment, at any time.
Traditional network-based security solutions focus on network protection and are blind to application context. With 72% of attacks targeting the app rather than the network, this really is the area organisations need to focus on.
F5’s ability to eliminate the blind spot caused by encryption provides necessary visibility and analysis for all application traffic, allowing you to make decisions based on the potential risk to the application and take necessary action. Also, F5 solutions are delivered where businesses need them—as software, standalone hardware, virtual appliances, and in the cloud, giving you greater flexibility.
Only with visibility into all the weak points attackers are exploiting within user identities and applications themselves, will enterprises like yours be able to protect data.
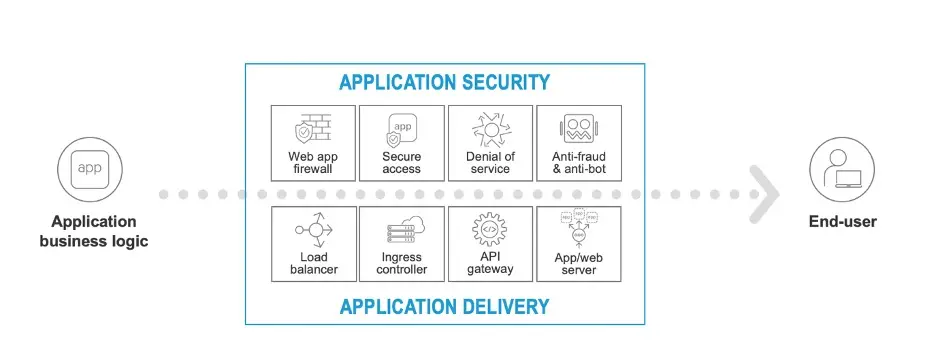
F5 has expanded the scope of its services with recent acquisitions of NGINX, Shape Technologies and Volterra. With these acquisitions it can deliver Application Delivery and Application Security services across the whole data plane between the code of the application to the user and from the core to the Edge 2.0
This allows organisations, from the smallest of SMB to the largest of global enterprises to choose the right solution set, licencing models and budgets to meet their needs.
F5 believe in the vision of Adaptive Applications, where applications can grow, shrink, defend and heal, based on environment and how they’re being used.
Application services include capabilities that facilitate application delivery, such as application servers, web servers, Ingress Controllers, load balancers, DNS lookup and CDN’s (Content Delivery Networks). In addition to this you have application security including WAF’s (Web Application Firewalls) secure application access, anti-DDoS, Anti-Bot, and defence against identity theft, fraud and abuse.
Each of these application services generate valuable data regarding latency, policy enforcement and steering, providing visibility to optimise performance and security by using change controls and configurations.
Adaptive Applications add an additional layer of analytics and automation using Machine Learning (ML) and Artificial Intelligence (AI) techniques that enable the system to learn from historical or similar traffic patterns and provides insight for optimisation, allowing resources to adapt, based on business needs.
“F5 are building an application serving platform that will fundamentally change the way applications are delivered and secured – ultimately helping customers deliver the differentiated digital experiences that have become so important for every organisation.”
Customers expectations are paramount to a growing business and expectations are high, speed, efficiency and security create the best customer experience.
Adaptive Applications:
- Automate redundant processes for greater efficiencies
- Expanding and contracting based on performance needs
- Protecting itself, securing points of vulnerability
- Getting smarter, more insightful, self-healing and evolving quickly
Key points of Adaptive Applications:
- Performance
- Security
- Automation
- Insight
Your organisation wants to provide great value to your customers but delivering a personalised experience can be challenging due to complex portfolio’s, evolving security threats and a lack of visibility.
“F5 can help secure and deliver extraordinary digital experiences by simplifying traditional application delivery, enabling modern app delivery to scale, securing every application wherever it is deployed, whether at the core or the edge, and using data to unlock the value of insights and automation.”
“F5 to create the 1st Edge 2.0 platform. Security First, application driven with unlimited scale”
F5 Solutions Overview
- Applications Security
- Online Fraud Prevention
- Network Security
- Access Control and Authorisation
Application Security Services
Traffic Management
- Load Balancing
- DNS Delivery
- Policy Enforcement
Application Security
- Web Application Firewall
- Identity & Access Management
- SSL Orchestration
Infrastructure Security
- L4 Firewall
- Anti-DDoS
Traffic Management
Traffic Manager: BIG-IP Local Traffic Manager enables you to control network traffic and select the correct destination based on server performance, security and availability.
BIG-IP LTM is a full proxy enabling you to inspect, manage and report on application traffic entering and exiting your network.
The SSL performance of BIG-IP LTM allows you to cost-effectively protect the end-to-end user experience, encrypting everything from client to server. Optimising the speed and reliability of your applications on both network and application layers. SSL Acceleration, real-time analytics, full elasticity, strong security and availability deployed in the cloud, hardware or virtual editions.
Application Security
Advanced Web Application Firewall (WAF): F5’s Advanced WAF protects your app’s with behavioural analytics, proactive bot defence, and application-layer encryption.
“F5 Advanced WAF can identify and block attacks that other WAF solutions miss.”
- Advanced Application Protection
- Proactive Bot Defence
- Anti-bot Mobile SDK
- In-Browser Data Encryption
- Behavioural DoS
- API Protocol Security
- Defence for the OWASP Top 10
- Stolen Credential Protection
F5 BIG-IP Access Policy Manager: Context-based application access to enhance security, usability and scalability. Employees and partners need remote secure access to business resources, whether from public or private cloud, mobile devices, as-a-service or on premise – Applications can be located and accessed anywhere, increasing the threat surface.
F5 BIG-IP (APM) secures, simplifies and centralises access to applications, API’s and data.
- Identity Aware Proxy (IAP)
- Identity Federation and SSO (Single-Sign-On)
- Secure Remote & Mobile Access
- API Protection
- Offload and Simplified Authentication
- Desktop Virtualisation Delivery
- Central Management & Deployment
- Performance & Scalability
SSL Orchestration: Over 80% of page loads are encrypted and attackers use encryption to hide malicious payloads, if you DO NOT inspect SSL/TLS traffic, attacks will happen and leave your business vulnerable.
SSL Orchestrator uses decryption/encryption of SSL/TLS traffic, protecting you from potential threats.
- SSL Visibility
- Dynamic Service Chaining
- Context Engine
- Granular Control
- Supports all Inspection Devices
- Supports all Deployment Modes
- Transparent & Explicit Proxy
- Extensive Logging
Infrastructure Security
L4 Firewall protects your network against incoming threats including DDoS attacks which could overwhelm your server, website or network and render it inoperable.
- Secure Your Data Centre
- Network Protection
- High-Volume Logging Controls
- Block Known Bad Actors
- SSH Channel Protection
- Flexible Defence of Complex Threats
- Data Centre Visibility
Anti-DDoS: DDoS Hybrid Defender is the only multi-layered defence that protects against blended network attacks and application attacks, while enabling full SSL decryption, anti-bot capabilities and advanced detection methods.
- Security & Scale
- Resilient Design
- Operational Efficiency
- Self-Tuning
- Built-in Intelligence
- Flexible Deployment
- Visibility
- Value
If you would like to know more about F5 or any of the above solutions, please get in touch.
We’re here to help you and your business create a secure future for customers, suppliers and your employees.
Digital Pathways Ltd are a Cyber Essentials Certified Business
Chat
Meet
New House Studio
Wood Mead
Epping
Essex
CM16 6TD

