Our Mission
To be a long-term trusted advisor to our clients for data encryption and cyber security confidence.
Our Vision
To provide our clients with solutions that are considered, rather than reactionary (to a breach), matched to the businesses way of working and scales as needed.
Our Values
To act with integrity, to always be honest and reliably provide diligent and competent services to our customers.
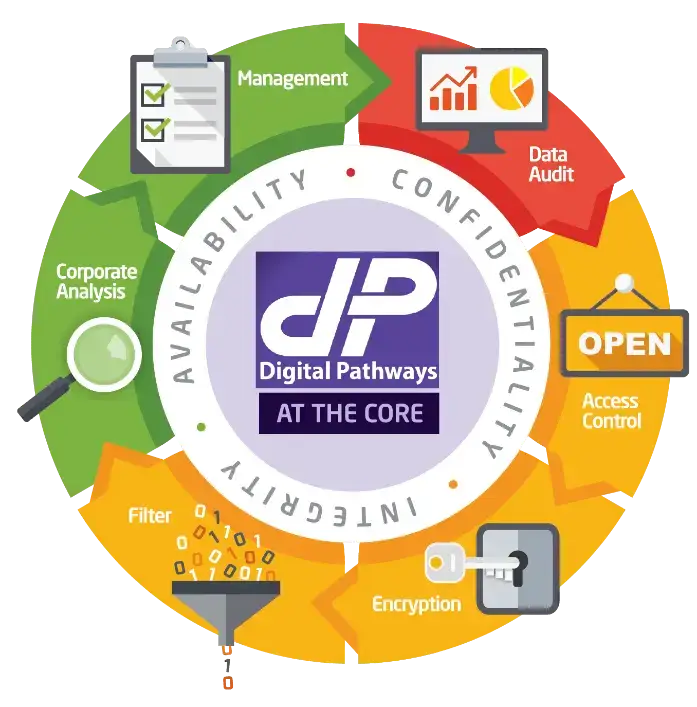
Our Methodology
Red – Stop
Discover and classify your data and check for vulnerabilities within the network or application. In order to properly assess risks, it is important to understand what data you have, how sensitive it is and where it is located.
Amber – Proceed with caution
Secure the data. There are many different ways to protect the data. Encryption coupled with good access controls is the starting point.
Green – Good to Go
Risks have now been assessed and controls implemented. Ongoing evaluation of your security posture should be monitored from system logs, network activity and user behaviour.
Our services encompass the ethos of confidentiality, Integrity and availability; the key to data security.