Definition “the process of converting information or data into code to prevent unauthorised access.”
Encryption is the most effective way to improve data security, by converting electronic data into another form; called ciphertext, which cannot be easily read or understood by anyone except the authorised parties who hold the specific key to decrypt the data back to plaintext. Therefore encryption protects the confidentiality and offers authentication and integrity of your data.

Why do we need Encryption?
In simple truth – Encryption should be the foundation of data security, in order to protect our data and information from being accessed and read by unauthorised parties. Businesses use it to prevent classified information getting into the wrong hands, from being shared with competitors, to protect personally identifiable information of employees and customers, for compliance and governance; as well as protecting against identity theft.
What are the benefits of Encryption?
Encrypted data is protected even if it gets into the wrong hands, therefore reducing the potential compliance and governance issues surrounding data privacy including GDPR. If all data is encrypted; whether it is at rest or in transit, and that data is lost or stolen the recipient cannot read the information. In essence, you are securing your crown jewels.
How should Encryption be used?
Encryption is the foundation of an organisations data security, whether your data resides in the cloud, on mobile devices or in a physical location. Breaking down data security silos by encrypting both structured databases and unstructured files, centralising key management across your organisation, along with providing privileged user access control, is a great starting point for data security. Digital transformation is having a huge impact on how we store and access information, we need to make sure that this is done securely.
We have produced a White Paper on Sensitive data and using encryption in conjunction with Fran Howarth, a leading data security analyst
Areas often covered with Encryption:
Please click on the links below to read more.
Managed Encryption Services
Full Disk Encryption
What is Full Disk Encryption?
Full disk encryption is achieved through software, hardware or a combination of the two. The primary purpose is to ensure the confidentiality of data on storage devices. As with all types of encryption, encryption key management and security is imperative so they must be secured within a tamper-proof environment. These environments are often referred to as Hardware Security Modules or HSM for short.
Full disk encryption is most commonly found on hard drives fixed into a laptop, PC or server, or removable media such as a USB drive or portable hard drive. Secure storage and transfer of data are the normal use cases for such technology.
Why have Full Disk Encryption?
The most obvious reason to apply full disk encryption is to mitigate against the unauthorised access to data resulting from the loss of a device. For example, a lost laptop ends up in the hands of an unauthorised individual. Without full disk encryption, an individual can remove the hard drive from the laptop. This hard drive can then be connected to a system and powered up, with potentially full access to the data. If full disk encryption were applied, the unauthorised individual would not be able to access the data without the password to decrypt.
Common offline attacks on this technology include brute force on the passphrase or key, attacks on the cryptographic implementation or algorithm used, search for plain text data on the device or physical tampering in order to read data or cryptographic keys.
All encryption and decryption processing is carried out on the device, and this must be coupled with software to manage user authentication. In the case of fixed disks, some solutions are able to offer pre-boot authentication as part of the decryption requirements. Full disk encryption requires compatibility with the host operating system, any endpoint security and storage interfaces.
Issues using Full Disk Encryption
One of the challenges of full disk encryption is enterprise management. Solutions exist to enable administrators to centrally manage policies (e.g. password complexity), account management (user provisioning), device recovery (key management & remote recovery) and to purge protected data.
Database Encryption
What is Database Encryption
Security auditors look for airtight security systems that prevent exploitation of vulnerabilities by adhering to a system of checks and balances to prevent the bypass of security controls. Implementation of strict security principles and adherence to organisational security policy may require that the Data Base Administrator (DBA) is prevented from accessing database audit logs or viewing rows or columns of data.
While the DBA is generally considered a ‘trusted’ party in regards to permitting access to information stored on databases, the ability of the DBA to access and, potentially, tamper with database audit logs conflicts with the separation of duties principle. Audit log files, therefore, must be stored outside of the database tablespace where the DBA cannot access them. Storing the files in an operating system directory, however, leaves the files outside the sphere of traditional database vendors protection, and vulnerable to access by other unauthorised users if not properly protected.
A security solution is needed to prevent exploitation of audit logs stored outside of the database domain.
Why is Database Encryption Important
IT administrators responsible for applications, networks and data management often require root privileges to perform their job duties. Root privileges may also provide them with the ability to access and view information which they do not have a need to know, especially when it conflicts with the organisation’s security policy, privacy legislation or industry best practices for the safe keeping of sensitive data.
With the increasing awareness of insider attacks targeting valuable information, this is a significant point of interest for auditors and security officers. The limitations of existing security solutions have made it unavoidable that anyone requiring root privilege is automatically awarded trusted status. Implementing effective internal security requires controlling the scope of root privileges and preventing root users from using operating system commands to view, copy or alter DBMS files. Any resource files located outside the control of the DBMS environment and potentially vulnerable to compromise should also be protected from unauthorised access and tampering.
Legislative and Regulatory Mandates
Recognition of the vulnerabilities to stored data has led to the passage of a variety of legislative and regulatory mandates targeted at ensuring security for personal and confidential information. Information stored on databases is frequently affected by these measures since personal data is most often organised into a structured format for convenient access and processing.
Data encryption, a commonly prescribed security measure that protects against unauthorised users accessing or copying sensitive data from storage or archives, can be a challenge to implement using Oracle or SQL once the DBMS and applications are operational. A robust encryption solution requires that encryption keys be stored in a secure location off of the host server where they cannot be obtained by hackers, and backed up for data recovery purposes. High performance is also a must to avoid an adverse impact on performance. A transparent, scalable, easy to install, and easy to manage encryption solution is needed to avoid disruption of IT operations.
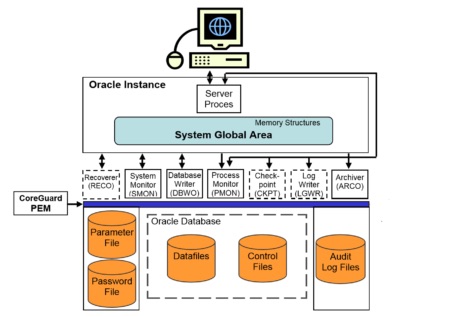
Scenario 1: Protected Oracle log, library and configuration files
In this scenario, Digital Pathways CoreGuard encryption has been added specifically to protect the audit log files and any configuration files located in operating system file directories. Locating the audit logs here removes them from the sphere of influence of the DBA in accordance with auditing or regulatory requirements. CoreGuard security can assure auditors and management that unauthorised system administrators, external attackers, or other unauthorised users are prevented from accessing and viewing the protected files.
Since CoreGuard takes a deterministic approach to protect data files by specifically associating authorised applications with protected data targets to identify the permitted accesses, any access attempts that are not specifically authorised are denied by default.
Users with root privilege can also be restricted from running OS commands to view or copy-protected data files. Any other potentially vulnerable configuration files located in an OS file directory could also be protected using a similar policy definition. Note that while creating and testing these policies, the policy can be run in Warn mode, whereby violations are alerted, but access is not denied, permitting adjustments to be made as required before locking down the protection policies.
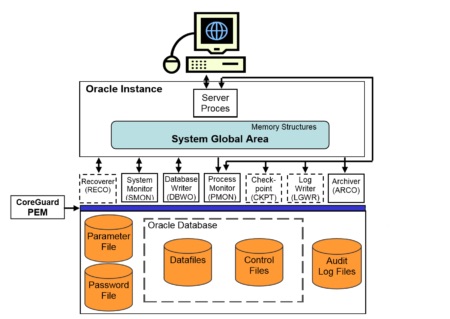
Scenario 2: Complete Oracle environment security
In this scenario, CoreGuard security has been expanded to lock down the Oracle (or any other database) environment, preventing any unauthorised persons or processes from bypassing Oracle security to access or alter protected data files.
Data protection policies are implemented that:
• Protect audit logs in the OS file directory (refer to Scenario 1)
• Protect resource files for Oracle and database applications
• Encrypt database files
Since data integrity is the overriding concern, rather than preventing unauthorised viewing of Oracle resource files, the Oracle resource files are cryptographically signed, but not encrypted. Database application resource files can be protected as well, providing that a CoreGuard PEM has been installed on the application host.
Protecting the database files themselves with encryption requires that the Oracle DBMS be able to access and view (decrypt) as required. Other applications, such as file backup, are provided with access privileges to the encrypted data files but are denied data viewing privileges. This ensures that administrators requiring data access to perform their jobs are provided with those privileges, but are not able to misuse their privileges to view database content.
Smart and Removable Device Encryption
Why worry about Smart and Removable Device Encryption?
There are many advantages to using removable media, chief among which is the quick and convenient means by which users can copy, transfer and backup data. This same ease of use is part of the problem, however, as malware is able to easily replicate and distribute themselves to unprotected removable storage devices, rogue programmes can be easily spread around a network going from one machine to another all from one removable device!
Any time that an employee copies sensitive data to removable media such as a USB, there is a risk of that data being accessed by unauthorised people.
Thefts of USB sticks are common in the Press and the fines for a loss can be high. British Airways was fined by the ICO, however now in the land of GDPR persistent losses could spark even bigger fines.
It is important to remember that once a device is no longer in your possession, you have no control over the data or who has access to it. Confidential information can then be transmitted to other parties or posted online for all to see. There are some devices and software applications that encrypt data on your device or media, giving you an added layer of protection in the event of your device getting lost or stolen.
Define a Policy
If you have removable media within your organisation the first step is to create a policy of acceptable use. The first step in the policy is the need to have a clear outline that explains the vulnerabilities of the company’s network, as well as the perceived risks that are associated with the use of removable media.
The next step is to clarify the purpose of your policy document. Here, you will explain what you wish to accomplish by having this policy in your environment so that users can understand what you are safeguarding by implementing these regulations. This is a great opportunity for you to encourage users to contact the IT department with any queries or concerns that they might have.
The policy will define when removal media can be used, and when it cannot. You must explain what data can be stored on such media, and how it must be copied. This is a good opportunity to explain anything from how to encrypt the information on the removable media, to how users must scan the media before it can be opened on their workstations.
Network-Wide control of media devices on machines can be deployed which will enforce:
• Encryption on any external devices plugged into a machine.
• Reject any unauthorised device being plugged into a machine
• Automatically scan the device prior to allowing any access to machine resources for malware or fileless attacks
• Totally disallow any device from being plugged into a machines USB port
As with any policy, it is important to monitor and alert on any unusual behaviour or breach of policy. Using analytics within the organisation is a key aspect to ensuring strong data security.
Folder & File Encryption
What is Folder and File Encryption?
Folder and file encryption is applied only to individual files or folders, also referred to as containers. The benefit of using this method of encryption is that only those files deemed as sensitive and requiring extra protection are encrypted. This means that the resource overhead is minimised.
How is Folder Encryption Deployed?
Folder and file encryption is normally enabled through a software agent being deployed to an endpoint such as a laptop or PC. The encryption agent is centrally controlled and managed. From here, enterprise-wide policies can be enabled to simply “encrypt everything”. Alternatively, and more efficiently, sensitive folders or file types can be identified and policies assigned to just these locations/extensions.
A more granular approach may be to allow the individual users to have more control over what they encrypt and thus a more locally managed approach is adopted. Software agents need only be deployed to the endpoints that store more sensitive data and as such, this is a more targeted approach to encryption.
How to Manage a File and Folder Encryption Strategy
The central administration of this method allows administrators to grant or revoke user access to encryption keys at any time. As always with encryption, the management and security of the encryption keys are of paramount importance.
Cloud Encryption
What is Cloud Encryption?
Compliance requirements and the penalties associated with them remain perhaps the single greatest set of drivers towards the adoption of cloud security technology. This includes the requirements for Data Privacy, the European Community General Data Protection Regulation 2016/679 (GDPR), other requirements which flow from compliance such as data residency.
Compliance is followed closely by the need to mitigate threats from breaches which may be driven by a broad variety of cloud threats. Finally, the need to address corporate security policies, which are derived from compliance as well as the need to protect against reputational damage provide strong incentives for customers to plan for, budget, and adopt the newest cloud security technologies.
As Gartner Group has noted the use of a cloud access security broker (CASB) can remediate and/or substantially address the security issues of cloud-based services or data storage.
How to Deploy a CASB+ Solution
The Digital Pathways CASB+ solution secures enterprise data as it is delivered to the cloud, without restriction on the cloud service or application. This is done in a way that is completely transparent to the cloud service end-users. Cloud application data is completely secured and protected through its entire lifecycle regardless of which SaaS, PaaS or IaaS you chose for your use.
We support multi-cloud environments with one unified and consistent Zero Trust approach. We secure all of your clouds, both SaaS, such as Salesforce, ServiceNow®, Office 365®, SAP® Successfactors®, Google® Apps, Box®, and Dropbox, and your custom cloud applications.
Zero Trust end-to-end encryption eliminates the risk of cloud threats and vulnerabilities, most of which you have no control over, to reduce your risk and ease of compliance. This unified and consistent approach reduces administrative costs and greatly reduces audit complexity. Cloud provider encryption is not only limited and insecure but also builds a silo for each cloud and increases complexity and costs for customers with multiple clouds.
Zero Trust
Zero Trust ensures that data is encrypted by the customer before it is delivered to the cloud, and only decrypted by the customer when being accessed by authorised users with additional security controls beyond standard login credentials. Any breach which intercepts or steals data at any point within the cloud only provides the attacker with unintelligible content as the data is encrypted. If the stolen data is encrypted, there is no breach to report for compliance purposes.
This end-to-end or Zero Trust encryption applies to the entire lifecycle of the data. This includes at-rest (in the database), in motion (moving through the network, in APIs, middleware, etc.), and in use. By encrypting data “outside” of the cloud, you are no longer subject to breach due to misconfiguration, access to data encryption keys, access to encrypted databases through an API, or any other primary cloud threat. Your data is locked down with data encryption keys held by the customer, such that an attacker cannot put the pieces together to access your data.
Zero Trust enables you to address the weakness inherent in broken SaaS application data security architectures, and meet the newest and most challenging data security demands of the latest compliance regulations.
The Digital Pathways solution’s based on the CASB+ standard encryption and key management architecture allows one global instance of a SaaS application to selectively encrypt the data for each required country and meet local residency requirements. This capability is provided while also meeting multiple countries’ requirements for residency using the same application instance and ensuring that identifying personal or sensitive data is not revealed outside of the country or area of sovereignty.
Mail Encryption
Why Secure Email
Sending traditional email has the confidentiality of a postcard.
The ICO (www.ico.org.uk) talk heavily about email encryption and why it should be used. We know from experience that many organisations send a lot of sensitive information about staff, contracts, mergers and IP information via email. Often this email is sent from online services such as Microsoft 365 and is stored, in the clear text, in the cloud. This means it is unprotected when it is in your cloud mailbox, and because cloud service providers do not warn you of attempts to access your online mailbox you never know if someone has got into your mail store!
Email is also a vehicle for data to be exfiltrated out of the organisation either deliberately or by mistake. Worse still you could breach compliance by sending via email information such as credit card numbers, banking details or PII data.
Protect Emails
Although only mentioned four times in the regulations, encryption is a significant aspect of information flow, GDPR specifically identifies ‘encryption’ as a potential and appropriate technical measure to ensure the security of personal data.
“In order to maintain security and to prevent processing in infringement of this Regulation, the controller or processor should evaluate the risks inherent in the processing and implement measures to mitigate those risks, such as encryption.”
GDPR is not prescriptive, it doesn’t define what is meant by encryption nor how it should be implemented. At the most basic level securing the transmission of data between your organisation and the recipient, the organisation is the baseline.
Transport Layer Security (TLS)
The Digital Pathways encryption Gateway provides support for the use of Transport Layer Security (TLS) as standard when emails are sent between organisations or individuals. If a user sends a secure email to an organisation it first checks to see if they are also using the solution if they are the email content is encrypted and the transmission, point to point is encrypted and the mail is delivered. If the end user is not using the system the email is encrypted but sent as secure webmail. The user is offered a link to receive the email and asked to sign into the service and they are then granted access to the email. Thereafter they will receive the email directly without needing to go to an online portal.
Encryption
Whilst ‘encrypting’ the transmission channel is a laudable first step, it still leaves the content that you are sending in a readable format. True encryption of the content is a natural progression and one that GDPR again references specifically around the mitigation of breach notification requirements.
Article 34 states that a breach notification to individuals is mandatory where it is likely to “result in a risk for the rights and freedoms of individuals”. However, if you can show that you have protected personal data adequately the impact of a breach can be minimised and the potential obligations reduced:
“…the controller has implemented appropriate technical and organizational protection measures, and that those measures were applied to the personal data affected by the personal data breach, in particular, those that render the personal data unintelligible to any person who is not authorized to access it, such as encryption.”
Digital Pathways Secure Email
Digital Pathways offers a cost-effective solution for secure email which is easily deployed and simple to use.
Digital Pathways Secure Email is available for many platforms and is scalable to meet any organisations needs.
Application Encryption
What is Application Level Encryption
Application level encryption takes a different approach than the more commonly adopted data at rest encryption. Application encryption occurs within the designated application and as such, often requires more preparatory work before being able to be deployed. This means that data is encrypted before it reaches the database.
Application encryption requires some coding to fully integrate into the application. Also, an API can be utilised where available.
How does it work
Application encryption allows for the encryption of specific fields within the application. This means that more granular access controls can be applied to the data.
One of the benefits of application-level encryption is that if a hacker manages to successfully access the database support, they would also need to have access (and valid credentials) to the application that was used to encrypt the data. This, therefore, adds a layer of protection.
If there is a need for multiple applications to access the database, this will complicate the key management process. This will also potentially have an impact on the performance of the database and prevent analytics on the data.
Masking
Data Masking
Gartner defines data masking as “a technology aimed at preventing the abuse of sensitive data by providing users with fictitious yet realistic data instead of real and sensitive data while maintaining their ability to carry out business processes.”
Where is Data Masking used
Masking of data is not actually an encryption method. In this case, the original data in the database is not encrypted. Through application integration, rules can be applied to sets of data to prevent users from seeing said data. A simple example of this is when you receive a letter from the bank which has your long 16 digit bank card number on it. However, only the last 4 digits are exposed. All the other digits are masked eg card number xxxx xxxx xxxx 1234. The same applies to computer systems. Not everyone needs to have access to all the data. They simply need to know that it exists or the format of it in order to maintain said data.
Masking also does not break the database schema so searches and analytics can still be run on the database.
One new variant is in dynamic masking
Static data masking is used in test and development environments where real data is required to test systems pre-release, while dynamic data masking is used in conjunction with operational data in real-time, such as in customer service desks. This involves dynamically intercepting requests to the database and masking any sensitive data row or column. Our solution offers the flexibility to establish varying levels of data redaction. Administrators can establish settings to have an entire field tokenized or to do dynamic data masking so only part of a field is visible in the clear. This is complementary to, or a replacement of, the sort of role-based access controls that are in use in many environments to prevent, for example, HR employees seeing the salary levels of executives.
Masking of data works in conjunction with a Tokenization server. Please see our page on Tokenization.
Where can Data Masking be used
Data masking can be used to protect various types of data, but some of the most used data in the business are:
Payment card information (PCI-DSS)
Protected health information (PHI)
Intellectual property (ITAR)
Personally, identifiable information (PII)
Pseudonymisation
What is Pseudonymisation
Pseudonymisation is generally associated with the European Union’s General Data Protection Regulation (GDPR), which calls for pseudonymisation to protect personally identifiable information and is the only technology specifically mentioned within the Act under “Article 4, Definitions”:
‘Pseudonymisation’ means the processing of personal data in such a manner that the personal data can no longer be attributed to a specific data subject without the use of additional information, provided that such additional information is kept separately and is subject to technical and organisational measures to ensure that the personal data are not attributed to an identified or identifiable natural person.
Pseudonymisation takes easily identified fields within a database or file and replaces them with artificial identifiers, or pseudonyms. For example, a car make is replaced with a unique number. The purpose is to render the information unrecognisable and therefore reduce concerns with data privacy.
Pseudonymised Data is not the same as Anonymised Data. When data has been pseudonymised it still retains a level of detail allowing tracking back of the data to its original form. Anonymised data is completely changed and thus cannot be reconstructed back to its original state.
Sensitive Pseudonymised Data should still be encrypted with a strong, industry recognised encryption program.
Where to use Pseudonymisation
The choice of which data is to be pseudonymised is sometimes company specific, but should always be Personally Identifiable Information (PII). Frequently such data is simply name, address, date of birth etc but could also include Social security or national insurance numbers.
The techniques used for Pseudonymisation depend on what you want to achieve and our solutions for Data at Rest Encryption, Tokenisation or Masking cover the most popular and industry recognised solutions to protect data. In our opinion, there is no point in deploying a simple form of data scrambling if the value of the data is so high that if there were a breach you would face a fine because the protection taken on the data was not in proportion to the data significance.
Tokenization
What is Tokenization
Tokenization makes it easy to use format-preserving tokenization to protect sensitive fields in databases. The solution features a Token Server, which is a virtual appliance for tokenizing records and managing access to tokens and clear-text data. With our Token Server, applications use REST APIs applied to the application being used to send requests for the creation and management of tokens, which streamlines the process of implementing and managing tokenization. In addition, the product eliminates the complexity of adding policy-based dynamic data masking to applications (please see our Data Masking page).
Advantages of Tokenization within the Enterprise
Tokenization delivers the following advantages:
• Streamlined application integration. The solution employs tokenization at the application layer and it streamlines all the application development efforts associated with implementing tokenization in an enterprise.
• Granular, flexible controls. Administrators can establish policies to return an entire field tokenized or dynamically mask parts of a field. For example, a security team could establish policies so that a user with customer service representative credentials would only receive a credit card number with the last four digits visible, while a customer service supervisor could access the full credit card number in the clear.
• Non-disruptive implementation. With the solution’s format-preserving tokenization capabilities, you can restrict access to sensitive assets, yet at the same time, format the protected data in a way that reduces the operational impact typically associated with encryption and other obfuscation techniques.
With the Digital Pathways Tokenization solution, you can capitalise on a range of features that streamline up-front implementation and ongoing operations:
• Enables efficient, enterprise-wide administration. With the capabilities offered by our Data Security Platform, you can choose from a range of technologies and employ the mix that’s optimally suited to your specific projects and use cases. At the same time, you gain the cost savings and operational benefits of working with solutions that can be centrally and uniformly managed. With our Data Security Platform, your organisation can centrally manage keys for Tokenization, as well as for Transparent and Application Encryption.
• Offers non-disruptive implementation. With the solution’s format-preserving tokenization capabilities, you can restrict access to sensitive assets, yet at the same time, format the protected data in a way that reduces the operational impact typically associated with encryption and other obfuscation techniques. For example, your organisation can tokenize a credit card field in a database, yet keep the tokenized information in a format that is compatible with associated applications. Further, you can create tokens that appear to be real credit card numbers, so tokenization does not break existing validation processes.
• Eliminates manual efforts and complexity. The solution employs tokenization at the application layer, and it streamlines all the application development efforts associated with implementing tokenization in an enterprise. With the solution, developers don’t have to manually institute identity management or redaction policies. Digital Pathways Tokenization offers an easy-to-use REST API for integration with the Token Server, so your application developers can simply and quickly add tokenization and dynamic data masking to applications.
Key Management
How to handle Encryption Keys
Applying encryption to secure data is a strong way to protect it. However, without strong key management, the control can be ineffective.
The concept of key management covers the secure storage, generation, rotation and deletion of the encryption keys. Key management can be a local activity relating to the specific database that has been encrypted. It can also be centrally managed where encryption has been adopted enterprise-wide across a variety of platforms, data sets, devices. In such circumstances, the key security and management are normally performed by a Hardware Security Module (HSM).
Cloud adoption is also a driver for centralised key management. This allows the separation of duty, splitting the key from the data. There are many compliance requirements for such good practice, and cloud adoption/migration can bring this issue to the forefront.
Data at Rest Encryption
What is Data at Rest Encryption
Data at rest encryption is a term used for the application of encryption technology to data that sits within databases, file systems and other storage devices. It specifically does not deal with data in transit.
How to use Data at Rest Encryption
Transparent Data Encryption (TDE) is one of the most common methods of data at rest encryption. It is used on databases where it encrypts at the structural level of the database. TDE uses a database encryption key to perform the encryption/decryption process. This key is stored in the database boot record. The management and security of multiple keys from multiple databases can prove troublesome. It is also good security practice to separate the key from the data. As such, enterprises often adopt centralised management of TDE, including key management and security.
Digital Pathways Ltd are a Cyber Essentials Certified Business
Chat
Meet
New House Studio
Wood Mead
Epping
Essex
CM16 6TD